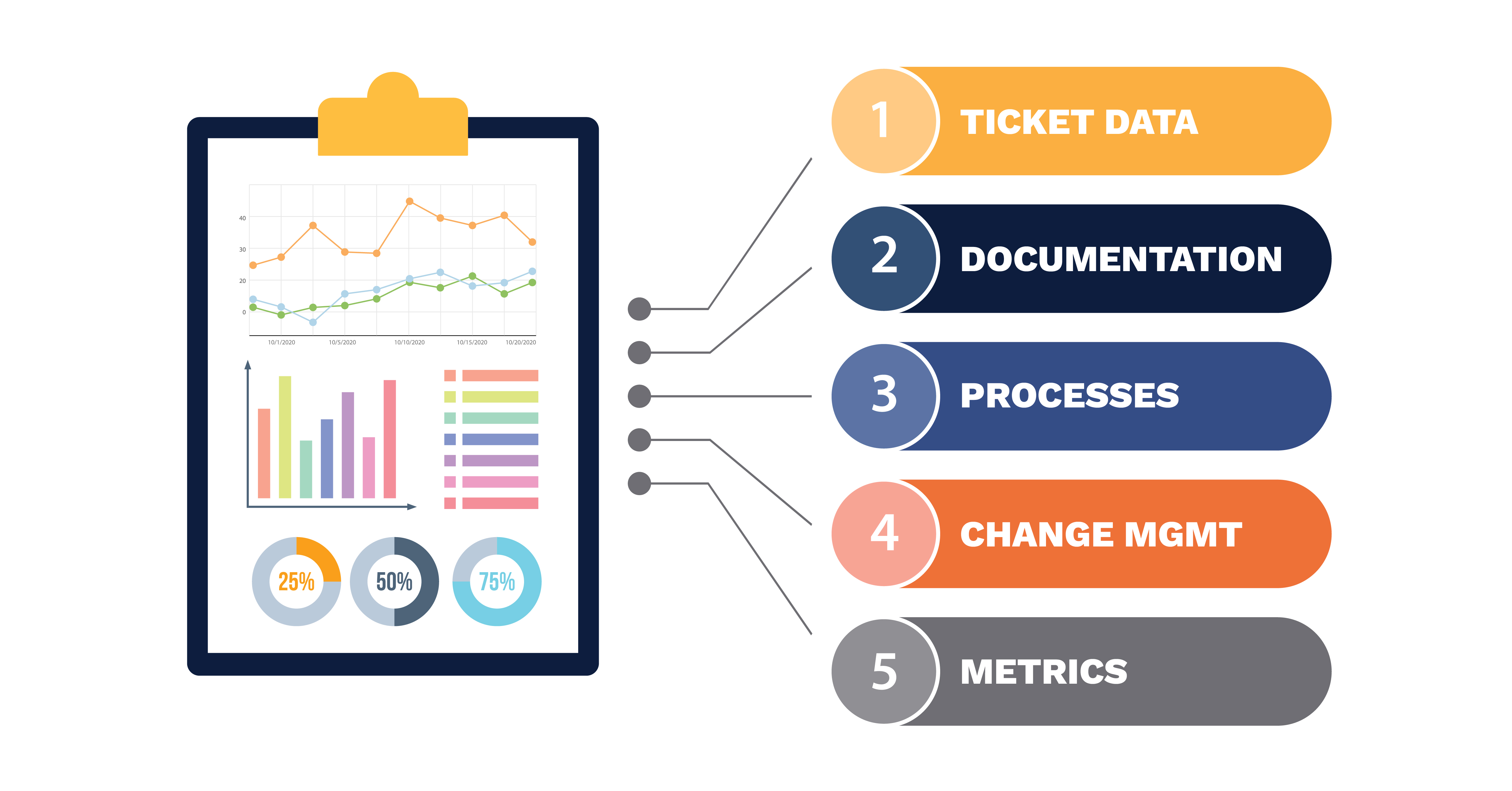
The MSP's AI Readiness Checklist: 5 Things to Fix Before You Deploy Anything
Here's something the AI vendor pitch decks won't tell you: most AI deployments that underperform aren't technology failures. They're preparation...
Get everything you need for the ultimate client experience
Enterprise-grade infrastructure with the flexibility MSPs demand
Perfectly tailored AI that knows your specific MSP

Build your own Shopify-like store with your PSA products & distributors
Have clients to submit tickets directly to your PSA, freeing up your team's time
Pre-triage and route tickets correctly with the help of AI
Deliver instant, accurate answers that can help achieve zero-touch resolution
You'll learn things like how to add revenue without adding cost, MSP best practices, and how to master client management.

The recent attack on Kaseya’s VSA product shows again the important role that IT support organizations play in selecting, deploying, managing and monitoring the technology stacks of their clients. Kaseya is not the first to be attacked, nor will it be the last. Kaseya is just the latest.
RMMs or other applications such as Microsoft’s Intune that provide management of remote servers and endpoints are essential in providing affordable and efficient service. Without these tools, per seat pricing would either be considerably more expensive or leave systems exposed to other vulnerabilities such as out-of-date operating systems, browsers or applications.
A proper technology stack combines tools that work together to minimize risk and include processes and procedures to follow if problems occur. The better the stack is designed, the less the impact from attacks or the faster recovery if it occurs. In financial terms, these multiple layers would be called a “balanced portfolio”. In a balance portfolio, if there are problems in one area, there are offsetting areas that step up to fill those gaps.
Unfortunately, IT service providers must create their own stack based on incomplete information from vendors. For example, Kaseya does not spend much time discussing the complementary strategies and tools that you will require given the inherent risks of the RMM. But it’s not just Kaseya - we have yet to see any RMM provider lead with the marketing message “Don’t worry about our tool until you have a good backup strategy in place!”
It is the intellectual property (balance, research, testing, procedures, etc.) included with a stack that makes up the value of an MSP’s per-seat pricing. Unfortunately, “smart” stacks and “dumb” stacks often look the same to the average client until problems occur and then it is too late to opt for the smarter solution.
Given that clients and end-users are not that interested or noticeable of all the details of a smart and well-researched stack, IT providers must find other ways to showcase their approaches including:
CloudRadial helps you with all these key pieces to make sure that your stack and your intellectual property is valued by clients.
In discussing a “smart” stack, it is important to understand what CloudRadial does to minimize risk in its own product and how it complements other tools in your existing stack.
The most frequent question that comes up is “If agents are the threats, why deploy another agent?” The simple answer is that we are not an agent like an RMM. The CloudRadial data agent can only do three things:
The data agent is designed for report-only. As a reporting tool it helps you see:
The data agent helps you (and your clients) see that your core protections are up-to-date and engaged.
Like the data agent, the desktop application has no functionality to make changes to the system and runs a separate browser instance of the CloudRadial website. All other websites and URLs are run through the endpoint’s default web browser where those URLs are controlled by the latest browser security and endpoint controls.
All of the CloudRadial infrastructure is hosted in Azure utilizing Azure’s exceptional security framework. We limit access internally as needed and restrict access through multiple layers of security. More information on our security is available at https://www.cloudradial.com/security
Security is no longer the responsibility of only vendors, partners and clients. Security is something all three groups must actively work together to achieve. Vendors to improve their security and enhance security offerings, partners to deploy their stacks correctly, and users to understand how their own actions can both prevent and identify threats.
CloudRadial’s information collection and archiving as well as its training tools help bring all the parties to the table to help shape strategies for the successful prevention, identification, and remediation of future breaches.
Security is too important to leave to any single entity. It takes everyone working together to create a workable solution. The MSP or IT provider role is more important than ever to create and manage this valued solution for clients.
Here's something the AI vendor pitch decks won't tell you: most AI deployments that underperform aren't technology failures. They're preparation...

Here's the thing about AI pilots that nobody in the vendor world wants to acknowledge: MSPs don't get to experiment freely. You're not a SaaS startup...

Let's get something out of the way early: when most MSP owners hear "AI for your service desk," they picture a chatbot. Some widget sitting on a...